#Multi-Functional Credential
Explore tagged Tumblr posts
Text
RAMCOA/TBMC vs conspiracy theories. If this ends up being too long for one part, I'll make a part 2
In my intro post, I said this. To some people, especially non-survivors or questioning survivors, it may be confusing to try to differentiate what RAMCOA/TBMC vs conspiracy theories. In this post, I'm going to touch on specific theories and compare them to the realities of RAMCOA/TBMC
TW: RAMCOA and TBMC with definitions and moderate detail, CSA
Section 1- What does RAMCOA and TBMC mean?
Note- I explain RA and OA before explaining MC/TBMC because i split the MC/TBMC explanation into two parts (programming and non-programming)
RAMCOA- An acronym for ritual abuse, mind control, and organized abuse
TBMC- An acronym for trauma or torture-based mind control
Ritual abuse- A combination of physical, emotional, and s/xual abuse meant to control and condition the victim's thoughts and behaviors. It is deliberate and performed the same way repeatedly. RA will typically involve specific abuse performed the same way on the same date every year. For example, a specific "ritual" is performed every year on the victim's birthday. Typically but not always religious, spiritual, and/or political in nature. Typically involves multiple victims and multiple perpetrators. May be multi-generational, performed exclusively within a single family, performed in a cult, tr/fficking ring, or other organization/group that may be religious and/or political and can be very large or very small, performed without the victim's parents knowing in places where children spend time, or more. Many people believe that RA cannot take place without MC, but not necessarily programming. When people think of RA, they think of satanic ritual abuse. It's important to note that RA can occur using any religious beliefs and non-religious beliefs as well. When RA is satanic, more often than not it's the concept of satan being used to create fear, guilt, and conflicting religious beliefs in the child, not satanic worship.
Organized abuse- This is an umbrella term for any abuse organized with multiple victims and multiple perpetrators. OA is deliberate. Every aspect is planned by the perpetrators. This is typically seen in cults, tr/fficking rings of any type, places where children spend time, and any type of high control groups. In the case of places such as churches, daycares, schools, and camps, this doesn't necessarily mean that the entire group/organization practices OA. It may be a specific group of workers. For example, in a large daycare: Most of the staff does their job properly. They take care of the children, play with them, do activities, etc. These workers don't abuse the children and aren't aware of the abuse taking place. However, there are three staff members who are all members of a tr/fficking ring outside of the daycare. They all had all the credentials necessary to work at the daycare years in advance because this was planned within the ring for years. They all applied for the job and got it. While working at the daycare, they take small groups of children into another room and perpetrate abuse that they film for the tr/fficking ring.
MC/TBMC- Acronym for Mind Control/Trauma or T/rture Based Mind Control. There are two types of MC: programming and non-programming
Programming- Programming needs to be started at a very young age in order to work. The child is repeatedly t/rtured to intentionally cause the child to dissociate and develop a DID system that is made to function to perfectly suit the abuser's needs. The child is given cues to perform a specific behavior and bring out certain alters.
Non-Programming- This can be done to someone of any age as it does not cause DID. Typically done to prisoners of war/political prisoners, long-term k/dnapping victims, long-term abusive situations, people indoctrinated in a cult or trafficked later in life or in an organization unable to program someone. It can include willfull compliance in an extremely abusive situation, Stockholm syndrome, brainwashing though abuse and t/rture, t/rturing a POW until they switch sides and become completely loyal to the group that is holding them prisoner.
Section 2- Common conspiracy theories used in the context of RAMCOA explained, debunked, and compared to RAMCOA
Note- All of these terms overlap and are often used interchangeably by theorists. If I say that theorists claim an aspect of one of these theories, it's safe to assume that aspect is a part of the other theories.
Project Monarch- Project Monarch is a theorized CIA subsection of MKULTRA. It was first suggested by Cathy O'Brien, a famous conspiracy theorist. After recalling memories under hypnosis, she claimed she was kidnapped and that her and her daughter were victims of PM. She claimed that PM was made of international child tr/fficking rings, dr/g barons, and satanists who used TBMC to make her and her daughter into s/x sl/ves. She accused US presidents and government officials from several countries of being a part of PM and accused Bush of abusing her directly. Over many years of in-depth investigations, experts criticized her claims for including absolutely no evidence and having many inconsistencies. She claims to have a total photographic recall but remembered nothing about the alleged kidnapping abuse. Her later memories were "recovered" under hypnosis, which has been scientifically proven time and time again to create false memories more often than not. In current days, theorists claim that celebrities are victims of PM.
The Illuminati/NWO- Historically, the Illuminati was a real Bavarian secret society in the Enlightenment era. However, it was ended and banned around 1785. In this context, the Illuminati and NWO is a term used to describe all of the international elite of the world including government and royal officials, celebrities, the world richest families and individuals, elite organizations, banks and financial brances of government, corportations (known as resource control), the education system, all organized religions, the media, and all types of government including secret services, military, police, courts, and prisons. Theorists claim that the illuminati is conspiring to acheive world domination and that they are actively programming every citizen through many methods (none of these methods are used in real MC because they're impossible. also, you can't indirectly program someone through the media and education). They also claim that celebrities sell their souls to the devil and are programmed. This entire theory is rooted in anti-semetism and is still blatantly anti-semetic to this day. You can read about why it's anti-semetic here: https://www.cairn-int.info/journal-revue-du-crieur-2015-1-page-128.htm I think it should be very obvious why this is fake. In terms of MC, some of the ways theorists claim the illuminati programs citizens is subliminal messaging in the media, 5G internet, micr/chips in v/cc/nes, and more. Simply put, programming requires prolonged physical t/rture. I think that says enough.
MK-ULTRA- MKULTRA was a very real thing- in the 1950s and 1960s. It ended in 1964. The MKULTRA subsection that ran the latest (as far as I know) was NAOMI. It ended in the 1970s and wasn't about MC. This one is gonna be short and sweet. If you were born anytime after around 1930-1940, you were not part of MKULTRA.
Section 3- Moral panics and other historical events used to deny RAMCOA and why they shouldn't be used to deny RAMCOA
Michelle Remembers- This was the book that sparked the satanic panic. In 1980, a psychiatrist and his patient wrote a book about the real therapy sessions with the patient, a woman named Michelle (who he later married) who went to him to be treated for depression. After screaming nonstop for 25 minutes and then speaking as a five-year-old, the psychiatrist spent over 600 hours hypnotizing her (I've already talked about why hypnosis is bad). In that time, Michelle "remembered" very extreme RA at the hands of a satanic cult. This was investigated for decades and there was absolutely no evidence. During an 81-day ritual in which Michelle claimed to be locked in a cage, she was attending school with no absences. She had no unusual absences any other time either. The extreme t/rture she claimed to have experienced involved her being t/rtured and c/t with kn1ves, and yet she had no scars. She claimed that during the 81-day ritual, they summoned Satan, Jesus, Mary, and Michael the Archangel who removed her scars. The most recent documentary about this book was this year. This book was used as training material for social workers and law enforcement, and the psychiatrist was called as a consultant in the McMartin preschool trial. This book has been used for years as proof for why you cannot repress and recover memories. But what it actually proves is that hypnosis can easily cause false memories, especially 600+ hours of it. Amnesia is a common symptom of trauma, and even more common for anyone with DID as different alters hold different memories. This book proved absolutely nothing about dissociative amnesia.
Satanic Panic and the daycare CSA hysteria - After Michelle Remembers was published, it was said that there were over 12,000 documented accusations of satanic ritual abuse in America that were investigated and proven false. The Kern County case started the daycare CSA hysteria. In 1982-1983, 60 children in Kern County claimed they had been abused by a satanic s/x ring. It started when two children were coached by their grandparents into saying their parents abused them as part of a satanic s/x ring. 36 people were convinced, but no evidence was ever found. The McMartin preschool trial was the second case. In 1983, a parent accused a teacher at McMartin of abusing her son. The school sent out a notice to the parents to check their children for signs of abuse. The mother was found to be a paranoid schizophrenic and an alcoholic, but not before 360 interviewed children claimed to have been abused at the preschool in incredibly bizarre, inconsistent and impossible manners. The way in which they were interviewed was found to have been very suggestive and confusing for the children. No evidence was found. The case lasted 7 years and costed $15 million, but no one was convicted. There were at least 16 famous cases that made up this hysteria. This is used to say that RAMCOA is just the satanic panic all over again and that false memories are made without hypnosis. What it actually proves is that children have active imaginations and are willing to say what adults and peers tell them to say. The children of these daycare trials had no idea what CSA and SRA were, they were claiming what parents, peers, and law enforcement suggested and coerced them to say. Also, it's been proven that researches were not able to implant memories of REPEATED CSA without the use of suggestion while on dr/gs and/or under hypnosis.
False memory syndrome + the false memory syndrome foundation- The False Memory Syndrome Foundation was an organization made to support people who had been accused of abuse after the accuser developed false memories because of therapy. It was founded by a Peter Fryd who was accused of CSA by his adult daughter, along with Pamela Fryd, Peter's wife AND ST3PSISTER. His daughter is Dr. Jennifer Freyd, the doctor who came up with DARVO and is an expert researcher in the field of betrayal trauma.
A founder of the foundation famously said in court and the media "60% of women s/xually abused in childhood reported that the experience was ‘good for them'".
Another member of the board gave an interview to a pro-"MAP" (i'm using the term instead of the real word because of guidelines) magazine. He stated " *MAPS* can boldly and courageously affirm what they choose. They can say that what they want is to find the best way to love. I am also a theologian and as a theologian, I believe it is God’s will that there be closeness and intimacy, unity of the flesh, between people. A *MAP* can say: ‘This closeness is possible for me within the choices that I’ve made.’”.
Another board member and medical professional stated when talking about therapy for CSA survivors "The real message being sold by these new therapy messiahs is the ultimate cry-baby solution to everyone’s pitiful human problems. It’s all someone else’s fault.”
And ANOTHER board member said “A friend and colleague had an adult daughter in therapy accuse him of childhood s/xual abuse.” She says, “It was my best judgment that this was unbelievable of the person I knew and could only been induced by the therapist.”. She said this while having no contact with the therapist or daughter.
Source: https://news.isst-d.org/the-rise-and-fall-of-the-false-memory-syndrome-foundation/ another good article: https://www.thecut.com/article/false-memory-syndrome-controversy.html False memory syndrome is a term used to describe simply having false memories. It was coined and used to describe people who recovered memories of abuse in therapy that didn't happen. However, according to the British Psychological Society stated that while researchers were able to implant memories of a single abuse incident, they were never able to implant memories of repeated abuse. Memory is highly suggestible and changes every second. Every memory you have has small details that've changed over time. Elizabeth Loftus and Jim Coan were able to implant memories 6/24 participants in of being lost in the mall as a child. Wade was able to implant memories of a hot balloon ride in 50% of participants. Loftus also implanted memories of being attacked by a small animal as a child, nearly drowning and being saved by a lifeguard as a child, and having a physical accident at a wedding as a child. She also proved that people viewing a video of a car crash would remember the crash differently depending on the wording used by the interviewer. Pezdek and Hodge tried to implant memories of a painful en3ma in children, but it almost never worked. NOBODY was able to implant long-term PTSD, somatic flashbacks, total flashbacks, fear of s/x, hypers/xuality, physical symptoms of CSA trauma, strange and overwhelming emotional responses and emotional flashbacks, s/bstance abuse, SH, hypervigilance or disinhibition, trauma disorders and co-morbid disorders, dissociation, etc etc.
#actually traumatized#trauma#ramcoa survivor#ramcoa#ramcoa system#tbmc#tw tbmc#programmed system#tw ramcoa#hc did
90 notes
·
View notes
Text
The Strategic Role of Check-in Kiosks in Military Airport Terminals

Military airport terminals operate under heightened security and efficiency demands compared to their commercial counterparts. These facilities not only handle routine transport of service members but also play crucial roles in logistics, emergency deployments, and diplomatic missions. In such high-stakes environments, even minor inefficiencies or security lapses can have significant consequences.
To meet these challenges, many military terminals are turning to check-in kiosk technology—automated, self-service systems that streamline passenger processing and improve terminal security. These kiosks, equipped with advanced features such as biometric scanning, real-time data synchronization, and user-friendly interfaces, are reshaping the operational landscape of military air travel. In this blog, we explore how kiosk technology enhances security, boosts efficiency, improves user experience, and supports long-term cost-effectiveness and emergency readiness in military airport terminals.
Enhancing Security Protocols with Check-in Kiosks
Security is paramount in military environments, and check-in kiosks significantly contribute to strengthening existing protocols. These kiosks do more than expedite the check-in process—they integrate seamlessly with military-grade security systems to ensure rigorous identity verification and real-time data updates.
Biometric Integration for Identity Verification
One of the standout features of military check-in kiosks is biometric integration. Fingerprint scans, iris recognition, and facial recognition ensure that only authorized personnel gain access to secured areas. These systems eliminate the risks associated with lost or forged ID cards and allow for multi-factor authentication, which is critical in sensitive operations.
Biometric data is instantly matched against military personnel databases and watchlists, providing a higher level of accuracy and preventing unauthorized access. The process is not only secure but also faster and less intrusive than traditional methods, offering a seamless experience for users.
Real-Time Data Synchronization with Security Networks
Check-in kiosks in military terminals are linked to centralized security networks, allowing for real-time synchronization of data. When a service member checks in, their identity, assignment, and travel itinerary are cross-verified with military systems to detect inconsistencies or threats.
This instant communication enhances threat detection and tracking capabilities, allowing security personnel to respond swiftly to anomalies. Furthermore, in the event of a security breach, kiosks provide critical logs and timestamps to aid investigation and resolution.

Increasing Operational Efficiency in Terminal Management
Military terminals operate around tight schedules and high throughput. By automating check-in procedures, kiosks alleviate common bottlenecks and enhance operational efficiency.
Automated Boarding Pass and ID Issuance
Traditional check-in desks involve manual data entry and document verification, which can slow down the boarding process. In contrast, automated kiosks issue boarding passes and temporary access credentials within seconds, drastically reducing processing time.
Kiosks can print, scan, and digitally store documentation, minimizing the likelihood of human error. This not only improves accuracy but also enhances compliance with standardized military travel protocols.
Reduced Staff Workload and Resource Allocation
By handling repetitive check-in tasks, kiosks free up human resources for more critical responsibilities. Personnel previously tied to desk duties can be reassigned to areas such as tactical operations, logistics support, or passenger assistance.
This optimized resource allocation ensures that the terminal functions more smoothly, even during peak hours or large-scale deployments. It also reduces the risk of operational delays, contributing to overall mission readiness.
Improving User Experience for Military Personnel and Visitors
Ease of use is crucial in high-pressure environments. Military check-in kiosks are designed with user-centric interfaces, ensuring accessibility for all users, including service members, dependents, and visitors.
Multilingual Support and Accessibility Features
Military airports cater to diverse users from various linguistic and cultural backgrounds. Kiosks equipped with multilingual options ensure that language barriers do not impede check-in or access.
Moreover, features such as voice commands, screen magnification, and wheelchair-accessible interfaces make these kiosks usable for individuals with disabilities. This commitment to inclusivity aligns with military values and enhances the overall user experience.
24/7 Availability and Minimizing Congestion
Unlike staffed check-in counters, kiosks offer uninterrupted service around the clock. This is especially beneficial in military operations where flights and deployments can occur at odd hours or on short notice.
By distributing the check-in load across multiple kiosks, these systems minimize terminal congestion, allowing for smoother passenger flow and reduced wait times. This is particularly valuable during mobilizations, drills, or emergency evacuations.
Cost-Effectiveness and Long-Term Savings
Implementing kiosk systems in military terminals requires upfront investment, but the long-term financial benefits make a compelling case for adoption.
Reduction in Manual Processing Costs
Kiosks reduce the need for manual data entry, paper forms, and physical staffing, all of which incur recurring costs. Digital processes streamline administrative workflows and lower the chances of clerical errors, which can be costly and time-consuming to fix.
In addition, kiosks help reduce the environmental footprint of military operations by minimizing paper use—a growing priority in defense logistics.
Scalability to Meet Future Demands
Modern kiosk systems are built with modular and scalable designs, allowing for future upgrades without major overhauls. As military travel protocols evolve, new software features or hardware modules (e.g., upgraded biometric sensors or contactless payment capabilities) can be easily integrated.
This future-proofing makes kiosk systems a strategic investment, capable of adapting to shifting operational needs and technological advancements.

Supporting Emergency and Contingency Operations
Military terminals must remain operational under all circumstances, including crises. Kiosks offer resilience and flexibility during emergencies, supporting both evacuation and redeployment efforts.
Rapid Reconfiguration for Emergency Protocols
In the event of a crisis—whether it’s a natural disaster, base lockdown, or global conflict—check-in kiosks can be rapidly reprogrammed to follow new protocols. For example, they can be configured to prioritize certain personnel categories, enable emergency passes, or facilitate health screenings during pandemics.
This capability allows terminals to maintain order and operational continuity, even in high-stress environments.
Reliable Communication Channels for Critical Updates
During emergencies, timely and accurate communication is essential. Kiosks can function as broadcast hubs, displaying critical alerts, evacuation routes, or mission updates directly on the screen.
Some systems can also send automated SMS or email updates to personnel, ensuring that everyone receives the necessary information regardless of their physical location within the terminal. This functionality is invaluable during fast-moving operations where traditional communication lines may be overloaded or unavailable.
Conclusion
Check-in kiosks are no longer just a convenience feature—they are a strategic asset in military airport terminals. From strengthening security with biometric authentication and real-time data sync, to improving operational efficiency and delivering a seamless user experience, kiosks represent a significant leap forward in military logistics technology.
They not only reduce costs and optimize personnel usage, but also enhance readiness and resilience during emergencies. With scalable architectures and support for the latest security features, kiosk systems are well-positioned to meet the future demands of military air transport.
For defense organizations aiming to modernize their infrastructure and improve mission efficiency, adopting kiosk technology is not just an option—it’s a mission-critical necessity.
#kiosk#technology#software#business#development#programming#productivity#airport#check in kiosk#tech#techtrends#selfservicekiosk#kioskmachine#innovation#kiosks#panashi#techinnovation#digitaltransformation
2 notes
·
View notes
Text
Perma-Bans, Petty Bans, and Poor Appeal Process
Recently I had my account banned for multi accounting. Now why would I be so pissed about this? Because the alt I had made was because of lost credentials and never interacted with the actual account I have, abandoned with literally two dragons in the lair the instant I got the creds for my real account back. But the account in itself isn’t where my peeve comes in. It’s the permanent ban of an active account after an alt was made two years prior. How was this alt found, you wonder? I sent a ticket in with the wrong email linked to my primary account asking about something related to copyright of FR on an upcoming project of mine. Okay that’s a little strange that I only got banned after I asked a question like that specifically, surely the appeal process will go fine when I provide context? Wrong! Even accused of funneling in the process (didn’t happen). What happens when the ticket staff are asked for receipts of said funneling? Permanent denial of response and ban stays in place. It genuinely goes over my head how genuinely abhorrent the process for handling potential multi-accounting is. I have met many people who have gotten away with very blatant funneling and multi accounting and willingly admitted it but are able to explain it away by lying in regards to something like siblings with shared devices. Even people who I personally have reported for funneling with verifiable evidence go untouched. How is this such a frequent issue? And why is it that people who make the most minor mistake of happening to make an account under a lost creds context gets all of their money and work zapped from them when people who do much worse in regards to TOS get off free? How is there no nuance to these situations by now? Are the staff just that petty and unwilling to work with the literal community that funds them? Why would making an account with zero work, interacts, etc be a constitution for a permanent account closure? Do the staff just not realize there is more punishment options than ‘oh you know what you lose it all, fuck you’? They have the ability to actually see context as clear by their forums punishment system, but refuse to take any strike actions on something with valid context? There’s so many other things that could be done, temporary bans, lockdowns on CR/AH, etc. But that’s just too difficult for them huh? What’s the damn point of the appeal function if they don’t actually bother to reconsider a choice? You cannot tell me either that gimmick accounts like nuzlocke form accounts aren’t also Alts. You would be a liar, and you would also be lying if you said that people don’t often make alts for ‘new starts. It’s honestly kind of funny at this point how many people ive heard the stories from who either got perm banned because they made an alt when they were like 14 and got banned 5 years later and stories of people actively funneling in major ways but haven’t been banned for years. The issue is so fuckin prevalent and yet half the time a ban happens because of it it’s for the most minor version of the rule break and almost never the people who actually violate the terms. “Economy advantage this, flight forums that” my ass. If the staff can’t hold even a small bit of understanding for such a minor issue which context resolves, maybe they don’t deserve the use of their site at all. Half the time I’ve seen staff interact with people they’re unbelievably rude and petty, especially Aequorian or whatever their name is. Always have to have a last laugh. But I digress. Maybe I’ll come back to my little account in 5 years time and appeal again and get denied. Kinda weird to think the accounts that had so much genuine time and effort dedicated into them are forced to rot for longer than they were ever active because of a faulty term of service and faulty enforcement of it.
24 notes
·
View notes
Text
Lifesaving Tech with Hidden Risks: Medical IoT Devices
Hey, so… what even are Medical IoT Devices?
Okay, let’s start with the basics. Medical IoT (Internet of Things) devices are basically smart gadgets that help doctors and patients manage health in real-time. Think of them as the Fitbits of the medical world, but way more advanced and sometimes implanted inside your body.
Here’s a quick rundown of the most common types:
Wearables: Smartwatches, glucose monitors, patches that track your vitals.
Implantables: Pacemakers, insulin pumps, neurostimulators that keep your heart ticking, your blood sugar in check, your brain functioning properly respectively.
Hospital Gear: Things like infusion pumps, ventilators, or MRI machines that are connected to the hospital’s network.
These devices are amazing because they can send data straight to your doctor, so they can monitor you without you having to camp out in a hospital bed. But (and there’s always a but), this connectivity comes with a price: security risks.
Wait, How Can a Pacemaker Get Hacked?
Okay, so let’s get into the nitty-gritty of how these devices can be exploited. It’s not just about “hackers being hackers”, there are specific technical flaws that make these devices vulnerable.
1. Encryption (or Lack Thereof)
Encryption is like a secret code that scrambles data so only authorized parties can read it. For medical IoT devices, encryption is crucial because they’re transmitting sensitive health data. But here’s the problem: not all devices use strong encryption.
What’s Happening: Some devices send data in plaintext (unencrypted) or use weak encryption algorithms that can be cracked by hackers.
Example: If an insulin pump sends unencrypted data to a doctor’s computer, a hacker could intercept it and alter the dosage instructions, potentially causing harm to the patient.
2. Authentication Protocols
Authentication is how a device verifies that someone (or something) is who they claim to be. Think of it like a password or a fingerprint scan. But many medical IoT devices use weak or default authentication methods.
What’s Happening: Devices might use hardcoded passwords (e.g., “admin” or “1234”) or lack multi-factor authentication (MFA).
Example: A hacker could use a default password to gain access to a hospital’s network of infusion pumps and change their settings, leading to incorrect medication doses.
3. Specific Attack Vectors
Let’s break down how a hacker might exploit a vulnerability in a real-world device, like an insulin pump:
Step 1: Reconnaissance
The hacker scans for vulnerable devices connected to the internet. Many medical IoT devices are discoverable through tools like Shodan, a search engine for connected devices.
Step 2: Exploiting Weak Authentication
The hacker tries default credentials or brute-forces the password to gain access to the insulin pump’s control interface.
Step 3: Intercepting or Altering Data
Once inside, the hacker can intercept data (e.g., blood sugar levels) or send malicious commands (e.g., delivering an incorrect insulin dose).
Step 4: Covering Their Tracks
The hacker might delete logs or use encryption to hide their activity, making it hard for healthcare providers to detect the attack.
This isn’t just theoretical. Researchers have demonstrated these attacks in controlled environments to highlight the risks.
Real-Life Examples That’ll Make You Side-Eye Your Smartwatch
Let’s talk about some real-world incidents that’ll make you go, “Oh no, this is actually happening”:
The St. Jude Medical Hack (2017): Researchers found that certain implantable cardiac devices had vulnerabilities that could let hackers mess with the device’s functionality. Imagine your pacemaker getting hacked and delivering random shocks to your heart. Terrifying, right?
The Hacked Pacemakers (2018): In a chilling demonstration, the FDA confirmed that nearly half a million pacemakers were vulnerable to hacking. Hackers could potentially alter the device’s settings, drain its battery, or even deliver fatal electric shocks. Abbott (the manufacturer) had to issue a firmware update to patch the vulnerability, but not all devices could be updated remotely, leaving some patients at risk.
Ransomware in Hospitals (2020): A ransomware attack on a German hospital disrupted its systems, and a patient who needed urgent care died because the hospital couldn’t operate properly. This wasn’t a direct attack on a medical device, but it shows how vulnerable healthcare systems are.
These aren’t just hypothetical scenarios. They’re happening, and they’re putting lives at risk.
Who’s Behind These Attacks?
Not all hackers are created equal. Here’s who might be targeting medical IoT devices:
Cybercriminals: They’re in it for the money. They might steal patient data to sell on the dark web or lock down hospital systems with ransomware.
Nation-States: Some governments use cyberattacks as a form of espionage or warfare. Targeting medical devices could be a way to destabilize a country or gather intel.
Hacktivists: These are hackers with a cause. They might attack a hospital to make a political statement or expose security flaws.
So… What Can We Do About It?
The good news is that there are ways to protect medical IoT devices. It’s not a lost cause...yet. Here’s what needs to happen:
1. For Manufacturers:
Stop Using Default Passwords: Imagine leaving your front door unlocked with a sign that says, “Welcome, hackers!” That’s what default passwords like “admin” or “1234” do. Manufacturers need to make sure every device has a unique, strong password right out of the box.
Lock Down Data with Strong Encryption: Encryption is like putting your data in a safe. Manufacturers should use the strongest locks available (like AES-256 encryption) to keep patient information safe from prying eyes.
Test for Weak Spots Before Selling Devices: Before releasing a device, manufacturers should hire ethical hackers to try and break into it. This is called penetration testing, and it helps find and fix vulnerabilities before they can be exploited.
Follow the Rules (FDA Guidelines): The FDA has a set of rules for making sure medical devices are secure. Manufacturers need to follow these guidelines to keep patients safe.
2. For Hospitals and Doctors:
Keep Medical Devices on a Separate Network: Think of it like having a VIP section at a concert. Hospitals should keep medical devices on their own secure network, away from the rest of the hospital’s systems. This makes it harder for hackers to sneak in.
Watch for Suspicious Activity: Hospitals should use tools that act like security cameras for their networks. These tools, called intrusion detection systems (IDS), can spot hackers trying to break in and alert the staff.
Train Staff to Spot Cyber Threats: Doctors and nurses are experts at keeping patients healthy, but they might not know much about cybersecurity. Hospitals should train their staff to recognize and respond to cyber threats, like phishing emails or suspicious device behavior.
3. For Patients:
Keep Your Device’s Software Up to Date: Just like you update your phone to get the latest features and security fixes, you should update your medical devices. These updates often include patches for known vulnerabilities.
Avoid Public Wi-Fi: Public Wi-Fi is like shouting your secrets in a crowded room, anyone can listen in. If your medical device connects to the internet, make sure it’s using a secure, private network.
Use a VPN for Extra Security: A VPN is like a secret tunnel for your internet traffic. It keeps your data safe from hackers, especially if you’re accessing medical information remotely.
The Bigger Picture: Why This Matters for Everyone
Okay, so this isn’t just a tech issue. It’s a public health issue. Vulnerable populations, like the elderly, people with chronic illnesses, or those who rely on medical devices to stay alive, are often the most at risk. And let’s be real: it’s not fair that some people are more at risk than others just because of their income or where they live.
Here’s the thing: wealthier patients might have access to the latest, most secure devices or private healthcare, while lower-income patients could be stuck with outdated or less secure options. Imagine needing a pacemaker but only being able to afford one that hasn’t been updated in years and is vulnerable to hacking. That’s not just unfair; it’s dangerous. And it’s something we need to fix as a society.
But it’s not just about money. There’s a bigger ethical responsibility here. Manufacturers need to prioritize patient safety over profits. That means investing in strong encryption, regular updates, and rigorous testing before releasing devices. And governments? They need to step up and enforce stricter cybersecurity standards to hold manufacturers accountable.
And let’s talk about the legal side for a sec. Laws like the FDA’s cybersecurity guidelines and the EU’s Medical Device Regulation are supposed to keep us safe, but they often lag behind the fast pace of tech advancements. Plus, there’s the whole question of liability: if a hacked device harms someone, who’s responsible? The manufacturer? The hospital? The patient? It’s a legal gray area that needs clarity.
Oh, and it’s not just a problem in wealthy countries. In developing nations, where healthcare systems are already stretched thin, a cyberattack on medical devices could be catastrophic. Access to secure healthcare is a basic human right, and we’re failing to protect that right when we ignore these vulnerabilities.
So yeah, this isn’t just about fancy gadgets or tech jargon. It’s about people’s lives. It’s about making sure that everyone, no matter their income or where they live, has access to safe, secure healthcare. And that’s something we all need to care about.
Final Thoughts
Medical IoT devices are a game-changer for healthcare, but their security flaws are a ticking time bomb. We can’t afford to ignore this issue, not when lives are on the line. Whether you’re a patient, a doctor, or just someone who cares about tech and ethics, it’s time to start paying attention.
So, the next time you hear about a smart pacemaker or a glucose-monitoring app, remember: with great tech comes great responsibility.
Further Reading
If you’re as obsessed with this topic as I am, here are some links to dive deeper:
MuddyWater’s Exploitation of Medical Devices (CISA Alert)
FDA Cybersecurity Guidelines for Medical Devices
Shodan: The Search Engine for Connected Devices
European Union Medical Device Regulation (MDR)
TL;DR
Medical IoT devices are amazing but have serious security flaws. Hackers can exploit these flaws to harm patients, and we need better safeguards to prevent this. Everyone (manufacturers, hospitals, and patients) has a role to play in making these devices safer.
2 notes
·
View notes
Text
starwalker42's fic masterlist ✨
A new masterlist because the old one was outdated. Please message if a link doesn't work! Tagging @today-in-fic
WIPs
Grounding Teen and up. Hurt/Comfort. After the traumatic events in Dudley, Scully is overwhelmed by everything that’s happened to her over the past few months. Mulder is there to help.
only one choice Explicit. A whole lotta smut. All my smut oneshots go here.
This Is Love Teen and up. Hurt/Comfort. Scully reunites with an abusive ex, and he threatens to turn her whole world back upside down.
One Shots
Birthday Blues Teen and up. Angst. <1K. It’s Mulder’s birthday, Scully is drunk, and emotions are coming out… but not the way they should be. Prompt from wtfmulder.
Coming Clean Mature. Angst. 3K. “Loving Mulder is as natural as breathing. It’s not lost on her that she’s currently underwater.“ Mulder and Scully deal with the fallout from the events of En Ami.
Consummation Explicit. First time smut. 4.5K. My take on Mulder and Scully’s first time, probably some time around Season 7.
Contact Teen and up. Romance. 3K. Five times Mulder touched Scully’s hand, and one time she touched his.
Dying Function, Living Key General audiences. Angst. 1K. Canon-divergent one shot based on speculation for Ghouli.
everything i know (brings us back to us) Teen and up. Angst with happy ending. 4K. Post-My Struggle III, Mulder and Scully need to talk. Maybe getting stuck out on the porch together is exactly what they need?
human credentials General audiences. Autistic!Scully fic. 4K. A realisation, a car ride, and a question.
Morning After Mature. Fluff. 1K. Exactly what it says on the tin: sweet, romantic morning after banter and fluff. Oh, and a piggyback. Prompts from anons and wtfmulder.
Together Explicit. Smut. 3K. “I’m never leaving you again.” Scully hadn’t realised how badly she needed to hear those words. He’s staying. He’s staying forever. “Prove it,” she whispers.
Multi-chapters
Agapi General audiences. Mulder-centric fic with moments throughout the series. 4K. or Five Times Fox Mulder Fell In Love. A one shot in five parts.
And The World Keeps Spinning Explicit. First time smut. 12K. Mulder and Scully’s first Valentine’s Day together as a couple (kind of!) and all the wonderful fluffiness (and smuttiness) that involves.
hard work Explicit. Sexting fic. 1.5K. A slightly different take on a prompt from the porn battle.
Maestitia Teen and up. Angst. Redux AU. 6K. “We’re going to lose her. I’m sorry.” Lose her. Another euphemism. No one can say it. Maybe if they keep avoiding the word they can pretend it won’t happen, that this isn’t what they all know it is.
Recovery Teen and up. Post-Tithonus Hurt/Comfort. 2K. Mulder and Scully work through Scully’s injury and what it means for them, together.
there will be darkness again - Teen and up. Angst/Whump. 14K. My take on the Febuwhump 2023 prompts.
Series
Sortis PG-13. Semi-abandoned. A collection of drabbles and snippets from throughout the years of Mulder and Scully’s relationship.
30 notes
·
View notes
Text

Congratulations to Amanda Westervelt! We are happy to announce that Amanda has accepted a promotion at PBEM. Here are the details from our director, Shad Ahmed:
I wanted to share some exciting news. Our own Amanda Westervelt—an attorney by training and an emergency manager at heart—rose to the top of a national open recruitment process and was selected for the recent Emergency Management Program Manager position at PBEM. A testament to her professional and personal dedication, Amanda began her time at PBEM as a NET volunteer, and leapt through the ranks, not only vertically, but also horizontally in roles across bureau programs. This required her to tackle new skills and program areas at every turn. She has yet to encounter a challenge she cannot navigate.
In this new role, she will join the PBEM Program Managers' team, as we continue supporting critical functions in an evolving mission. Most recently, she successfully helped conduct an exercise with over 70 partners from across federal, state, and local jurisdictions in an extremely short turnaround time. She is continuing to support the City's involvement in the national IronOR exercise, as well as taking on numerous other projects in areas such as the Duty Officer program and EOC operations.
Amanda's bio: Amanda Westervelt joined PBEM in 2021 after careers in biochemistry and then law, where she was the managing attorney for a satellite office of a multi-state firm. She grew up in rural Oklahoma, and ultimately moved to Portland in 2010, spending time at home to bring two beautiful children into the world and co-lead a very active Girl Scout troop. Amanda discovered emergency management through PBEM’s Neighborhood Emergency Team program and founded an advanced training event called NETCamp in 2019, the same year she joined the Oregon State Bar. When COVID hit, she was starting her own law firm, and pivoted instead to help run the Portland Mask Project and the NET Vaccine Access Project for PBEM and the Portland COVID response effort. Amanda has been certified as a hazardous materials technician, an EMT, and is currently a wilderness first responder and is certified to instruct a variety of first aid classes through HSI and emergency management classes through the State. Amanda has an undergraduate degree in biology from Cornell University, a juris doctor from Wake Forest University’s School of Law, and is working on her Master Exercise Practitioner credential from FEMA’s National Disaster and Emergency Management University.
Please join us in congratulating Amanda on her new role and please feel free to pass this message on!
3 notes
·
View notes
Text

Ahead of the Enthronement, The Queen & The Prince Consort have taken official portraits in the newly renovated Ambassadors’ Hall at the Palais Royal.

The Hall is one of many State and semi-state rooms undergoing renovations as part of the multi-phase project at royal residence. Originally known as The Gallery, a space between the royal private and public quarters where ambitious courtiers and citizens petitioned the monarch, it became the official space where dignitaries are received and ambassadors present their official credentials. During the reign of Louis XIV, The Gallery held an additional function for the Petit and Grand Levées and receiving deputations from Parlement before the Throne Room was added.
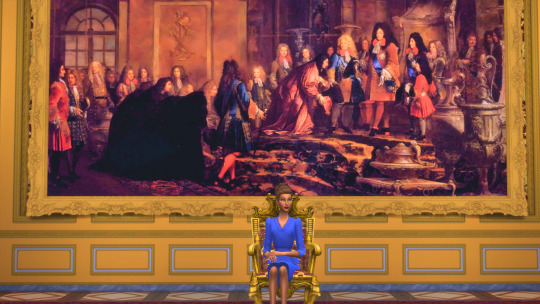
In his “Deputation from Parlement,” Baroque painter Jules-Baptiste Laurent captures a moment in a large painting, now displayed in the Ambassadors’ Hall and pictured in these new images.

#genevria#kingdom rp#sims4#royalsim#sims4rpblog#simsta#royalfamily#sims 4 legacy#sims 4 gameplay#sims 4
2 notes
·
View notes
Text
Millennium Semiconductors - Leading Innovation and Powering the Future
Millennium Semiconductors India Pvt. Ltd.: Pioneering Excellence in Electronic Components Distribution.
With an illustrious journey spanning 28 years, Millennium Semiconductors India Pvt. Ltd. stands as a beacon in the domain of electronic component distribution. Our portfolio encompasses a diverse range of active, passive, wireless communication, power, and electromechanical products and Specialty Chemicals and Materials.
What sets us apart is our unwavering commitment to operational excellence paired with innovative business solutions, ensuring we not only meet but exceed our customers' expectations.
Credibility & Recognitions: As an ISO 9001:2015 certified company, our credentials are further accentuated by recognitions from esteemed institutions such as Dun & Bradstreet, CRISIL, and the distinction of being a Great Place to Work.
Our Distinctive Edge:
• R&D Centre: Spearheading innovations and advancements.
• Design Excellence: From the nascent concept to prototype or production, tailored to specific needs.
• Optimization: Upgrading designs for enhanced features and cost-effectiveness.
• Re-engineering: Revamping projects for cost reductions and functional enhancements.
• Component Expertise: Recommending proven components for precise applications and providing embedded design support.
• Training Initiatives: Collaborative technical sessions with suppliers to enhance product understanding.
• IoT Enablement: Driving the future with IoT solutions for industrial and smart devices.
• Robust Supply Chain: Ensuring consistent and timely deliveries.
• Flexible Billing: Offering multi-currency billing options.
• Systematic Approach: Leveraging tools like Salesforce, SAP S4 Hana, WMS, and our dedicated Customer Portal.
At Millennium Semiconductors, our essence is to provide a holistic solution, affirming our position as the premier choice in our domain.
Millennium Semiconductors, we're not just a provider; we're your partner in progress.
For More Details Visit - https://www.millenniumsemi.com/
2 notes
·
View notes
Text
How Myofascial Courses Can Transform Your Approach to Pain Management

As the health and wellness industry evolves, professionals are turning to more holistic, integrative techniques to help clients and patients manage chronic pain and movement dysfunction. One of the most impactful tools in this space is myofascial release therapy — and by enrolling in specialized myofascial courses, practitioners can unlock a deeper understanding of the body’s connective tissue and its role in lasting pain relief.
Whether you're a massage therapist, physical therapist, personal trainer, or wellness coach, gaining skills in myofascial techniques can transform both your practice and your results.
What Is Myofascial Release?
Myofascial release is a form of manual therapy that targets the fascia — the web-like connective tissue that surrounds and supports muscles, bones, and organs. When fascia becomes restricted due to trauma, inflammation, repetitive use, or poor posture, it can lead to pain, limited range of motion, and reduced function.
Myofascial techniques involve applying sustained, gentle pressure to these restrictions, allowing the tissue to lengthen and return to a more functional, pliable state.
Why Take Myofascial Courses?
Myofascial courses provide in-depth training on how to identify fascial restrictions and apply therapeutic techniques safely and effectively. These programs are ideal for professionals who want to:
Expand their treatment options for chronic pain and mobility issues
Deepen their understanding of anatomy and fascial systems
Integrate fascia-focused work into massage, physical therapy, or fitness sessions
Deliver more lasting relief for clients struggling with soft tissue dysfunction
Increase client satisfaction and referrals by offering specialized care
Key Benefits of Myofascial Training
1. Elevate Your Clinical Results
By learning how to address the root cause of pain — often buried in layers of fascia — you can help clients experience deeper, longer-lasting relief compared to traditional massage or physical therapy alone.
2. Broaden Your Client Base
People suffering from chronic pain, sports injuries, fibromyalgia, TMJ dysfunction, or post-surgical scarring often seek myofascial release as a solution. With certified training, you become better equipped to serve these populations.
3. Boost Professional Credibility
Certification through reputable myofascial courses enhances your credentials and gives clients confidence in your advanced skills. It can also fulfill continuing education requirements (CEUs) for licensed professionals.
4. Improve Personal Body Mechanics
Many myofascial courses include training on practitioner ergonomics and energy conservation, helping you work more efficiently and avoid burnout or repetitive strain.
What to Expect in Myofascial Courses
While formats vary, most high-quality myofascial programs include:
Hands-on technique training (palpation, pressure, positioning)
Anatomy of fascia and the myofascial system
Assessment strategies for identifying fascial restrictions
Treatment protocols for different body regions (e.g., neck, shoulders, hips)
Real-world case studies and practice sessions
Integration with other modalities, such as massage therapy, physical therapy, and movement coaching
Courses may range from beginner to advanced levels and are often available as weekend workshops, multi-day intensives, or part of continuing education programs.
Popular Myofascial Techniques Taught
John F. Barnes Myofascial Release (MFR)
Structural Integration and Rolfing-inspired approaches
Trigger point therapy and deep tissue release
Myofascial unwinding and active release techniques
Fascial stretching and movement therapy
Who Should Take Myofascial Courses?
These courses are perfect for:
Massage Therapists (LMTs)
Physical Therapists and PT Assistants
Occupational Therapists
Chiropractors
Athletic Trainers
Personal Trainers and Strength Coaches
Yoga or Pilates Instructors
Manual Therapists and Bodyworkers
Anyone who works with the human body — especially in pain management, movement, or rehabilitation — can benefit from myofascial education.
Final Thoughts
Investing in fascia training courses is more than just professional development — it’s a commitment to delivering better care, deeper healing, and more effective pain management for your clients. As fascia becomes more widely recognized for its role in movement and dysfunction, those with specialized training will be at the forefront of a more integrative and results-driven approach to health.
If you're ready to elevate your practice, stand out in your field, and change lives — start exploring myofascial courses today.
0 notes
Text
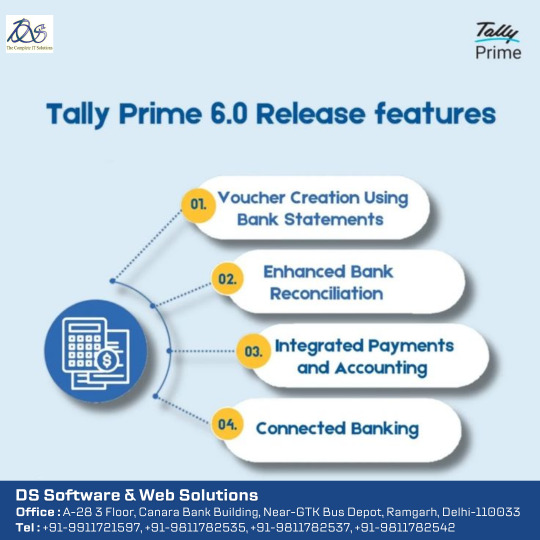
TALLY PRIME 6.0 RELEASE FEATURES
Here’s a comprehensive overview of the new capabilities in TallyPrime 6.0, officially released on 9 April 2025
1. Connected Banking & Automation:-
Real‑time bank integration: Connect securely to your bank using Tally.NET credentials to view live balances and statements inside Tally.
Auto‑voucher creation: Import bank statements to automatically generate payment/receipt vouchers with full details (narration, instrument no/date), in bulk or merged.
Smart reconciliation & e‑payments: One-click matching with rule-based and bulk options; create and track NEFT/IMPS payment files via e-Payment module supporting 18+ Indian banks.
2. Enhanced Banking Reports & Dashboards:-
New Banking Activities dashboard tile: shows pending reconciliations, balances, e‑payment statuses with drill-down reports.
Improved reporting in vouchers/day‑books, capturing bank account, instrument and reconciliation status; detailed Edit Log now tracks changes to UPI, bank date/instrument.
3. Streamlined Data Split & Verification:-
Simplified Data Split: new interface with enhanced options—single or dual company splits, progress bar, and robust pre‑split verification.
Resolves memory glitches and errors during large data operations .
4. Profile Management & Notifications:-
In‑app Profile section: modify contact info tied to serial number directly in Tally.
Semi‑annual reminders ensure your contact details stay current.
5. GST, TDS, VAT & Tax Enhancements:-
GSTR‑1 improvements: smarter filing with Excel Utility v5.4 for GSTR‑3B and breakup of B2B/B2C HSN summaries (Phase III from 1 April 2025).
Enhanced TDS/VAT reporting: precise calculations and correct state-wise reporting.
GCC compliance: bilingual (English/Arabic) invoicing, Arabic numerals, VAT formats for Kuwait/Qatar.
6. Income‑Tax & Regulatory Updates:-
Updated support for Income-Tax slabs under the 2025–26 Finance Bill, including rebate (87A), marginal relief, revised Form 16/24Q annexures.
7. Developer (TDL) Enhancements:-
New attributes & functionality: Skip-Forward, Disable Period on Tile, Multi‑Objects, IsPatternMatch, and Recon Status collection filter.
Internal optimization: Opening BRS details moved out of bank master to improve performance.
#tallyprime#tally on cloud#accountingsoftware#tallysoftware#cloud accounting software#cloudcomputing
0 notes
Text
What Defines a Truly Secure Website?

In today's digital landscape, a website is often the front door to a business, a personal brand, or vital information. With cyber threats constantly evolving, the question isn't just "Is my website online?" but "Is my website truly secure?" Many users look for the padlock icon and "HTTPS" in the address bar and breathe a sigh of relief. While essential, that green lock is merely the beginning of true website security.
HTTPS signifies that the connection between your browser and the website's server is encrypted, protecting data in transit. But a truly secure website goes far beyond encrypting data between two points. It's built on a multi-layered defense strategy, addressing vulnerabilities at every level of the application and infrastructure.
So, what are the characteristics of a website you can genuinely trust?
1. Always Uses HTTPS with Strong TLS Protocols
This is the foundational layer, but its proper implementation is crucial.
What it is: HTTPS (Hypertext Transfer Protocol Secure) encrypts the communication between the user's browser and the website's server using TLS (Transport Layer Security, the modern successor to SSL) certificates.
Why it's essential: It prevents eavesdropping, tampering, and message forgery, ensuring that the data you send (like login credentials or credit card numbers) and receive remains private and integral. Modern browsers flag sites without HTTPS as "Not Secure." Crucially, truly secure websites use strong, up-to-date TLS versions (like TLS 1.2 or 1.3), not older, vulnerable ones.
2. Robust Input Validation and Output Encoding
These are fundamental defenses against some of the most common web attacks.
Input Validation: Every piece of data a user submits (forms, search queries, URLs) must be strictly validated before the server processes it. This prevents attackers from injecting malicious code (e.g., SQL Injection, Command Injection) that could manipulate the database or execute commands on the server.
Output Encoding: Any data retrieved from a database or user input that is displayed back on the website must be properly encoded. This prevents Cross-Site Scripting (XSS) attacks, where malicious scripts could be executed in a user's browser, stealing cookies or defacing the site.
3. Strong Authentication & Authorization Mechanisms
Security starts with knowing who is accessing your site and what they are allowed to do.
Authentication:
Strong Password Policies: Enforce minimum length, complexity (mix of characters), and disallow common or previously breached passwords.
Multi-Factor Authentication (MFA): Offer and ideally mandate MFA for all user accounts, especially administrative ones. This adds a critical layer of security beyond just a password.
Secure Session Management: Use secure, short-lived session tokens, implement proper session timeouts, and regenerate session IDs upon privilege escalation to prevent session hijacking.
Authorization: Implement the principle of least privilege. Users should only have access to the data and functionalities strictly necessary for their role. Role-Based Access Control (RBAC) is key here, ensuring a customer can't access admin features, for instance.
4. Regular Security Updates & Patch Management
Software is complex, and vulnerabilities are constantly discovered.
Continuous Patching: The website's underlying operating system, web server software (e.g., Apache, Nginx), Content Management System (CMS) like WordPress or Drupal, plugins, themes, and all third-party libraries must be kept up-to-date with the latest security patches.
Why it's essential: Unpatched vulnerabilities are a common entry point for attackers. A truly secure website has a rigorous system for identifying and applying updates swiftly.
5. Comprehensive Error Handling & Logging
What happens when things go wrong, or suspicious activity occurs?
Generic Error Messages: Error messages should be generic and not reveal sensitive system information (e.g., database connection strings, file paths, or specific error codes) that attackers could use to map your system.
Robust Logging: All security-relevant events – failed login attempts, successful logins, administrative actions, suspicious requests, and critical system events – should be logged. These logs should be stored securely, centrally, and monitored in real-time by a Security Information and Event Management (SIEM) system for anomalies and potential attacks.
6. Secure Development Practices (SDL)
Security isn't an afterthought; it's built in from the ground up.
Security by Design: A truly secure website is born from a development process where security considerations are embedded at every stage – from initial design and architecture to coding, testing, and deployment. This is known as a Secure Development Lifecycle (SDL).
Code Reviews & Testing: Regular security code reviews, static application security testing (SAST), and dynamic application security testing (DAST) are performed to identify and fix vulnerabilities before the code ever goes live.
7. Web Application Firewall (WAF)
A WAF acts as a protective shield for your website.
What it does: It monitors and filters HTTP traffic between the web application and the internet. It can detect and block common web-based attacks (like SQL injection, XSS, DDoS, brute-force attempts) before they reach the application.
Why it helps: It provides an additional layer of defense, especially useful for mitigating new threats before a patch is available or for protecting against known vulnerabilities.
8. Data Encryption at Rest
While HTTPS encrypts data in transit, data stored on servers needs protection too.
Sensitive Data Encryption: Databases, file systems, and backups containing sensitive user information (passwords, PII, financial data) should be encrypted.
Why it's important: Even if an attacker manages to breach your server and access the underlying storage, the data remains unreadable without the encryption key, significantly mitigating the impact of a breach.
9. Regular Security Audits & Penetration Testing
Proactive testing is key to finding weaknesses before malicious actors do.
Vulnerability Scanning: Automated tools scan your website for known vulnerabilities.
Penetration Testing (Pen-Testing): Ethical hackers simulate real-world attacks to exploit vulnerabilities, test your defenses, and assess your overall security posture. These should be conducted regularly and after significant changes to the website.
10. Clear Privacy Policy & Data Handling Transparency
While not a strictly technical security feature, transparency builds user trust and demonstrates responsible data stewardship.
What it includes: A clear, easily accessible privacy policy explaining what data is collected, why it's collected, how it's used, how it's protected, and who it's shared with.
Why it matters: It shows commitment to data security and respects user privacy, a fundamental aspect of a truly trustworthy online presence.
A truly secure website is not a static state achieved by checking a few boxes. It's a continuous commitment to vigilance, proactive measures, and a deep understanding that security is an ongoing process involving people, technology, and robust policies. In a world where digital trust is paramount, building and maintaining a genuinely secure website is an investment that pays dividends in reputation, customer loyalty, and business continuity.
0 notes
Text
How Redevelopment in Mumbai Works: A Step-by-Step Guide for Mumbai Residents
Mumbai, a city known for its fast-paced growth and bustling life, is constantly evolving. Over the decades, the skyline has transformed, with towering buildings and state-of-the-art infrastructures replacing older structures. As Mumbai's population continues to grow, urban planning and real estate development have become key to its expansion. One significant aspect of this development is redevelopment—the process of renewing old, deteriorating buildings to make way for modern, safer, and more sustainable structures.
Redevelopment in Mumbai plays a vital role in addressing the city's housing shortage and improving living standards. It not only provides residents with upgraded homes but also revitalizes entire neighborhoods, boosting the city's overall aesthetics and functionality. Over the years, the rise of redevelopment projects has helped reshape Mumbai into a modern urban hub while maintaining its rich cultural heritage.
In this guide, we’ll walk you through the step-by-step process of how redevelopment works in Mumbai, from the initial stages to the final handover of homes.
Step-By-Step Guide On How Redevelopment in Mumbai Works
Redevelopment in Mumbai is a multi-step process that involves a series of stages, from identifying eligible properties to completing the final construction. Understanding this detailed process is crucial for residents who are part of a redevelopment project. Here’s a more comprehensive guide:
1. Identifying Eligible Properties
Redevelopment typically targets old, dilapidated, or structurally unsafe buildings, especially those that have been around for 30-40 years or more. These properties are often located in prime areas where the land value is high, making them viable for redevelopment. The first step is to inspect the building’s condition, and once a decision is made, a structural audit may be conducted to confirm its need for redevelopment.
2. Forming the Society Agreement
The success of any redevelopment project hinges on the consent of the residents. To begin the redevelopment process, the residents’ housing society must be formed, which can be a cooperative or a registered society. The society’s agreement with a developer is essential. Residents must meet and vote for the proposed redevelopment, usually requiring a 70-75% approval vote from the residents for the project to move forward. Without this consent, the project cannot proceed.
3. Choosing the Developer
Once the society agrees on the redevelopment, they can invite bids from developers to handle the project. The developer chosen must have a strong track record and reputation for completing successful redevelopment projects in Mumbai. The residents often form a committee to evaluate proposals and negotiate terms with the developers. This process can take time, as it involves carefully assessing the developer’s credentials, project design, and the compensation offered to residents.
4. Signing the Development Agreement
After a developer is selected, the next step is to sign the Development Agreement. This legal document is a binding contract between the residents’ society and the developer. It outlines crucial aspects such as:
The developer’s responsibilities during the redevelopment process.
The timeline for demolition and construction.
The compensation, which usually includes an upgraded flat for each resident (often with additional carpet area or better amenities).
Temporary housing arrangements for residents during the construction phase.
Terms related to the developer's obligation to maintain the building post-construction.
5. Obtaining Necessary Permissions and Approvals
Before any demolition work begins, the developer must obtain approvals from various government bodies. These include:
Brihanmumbai Municipal Corporation (BMC): The BMC approves the project’s plan, building permissions, and ensures compliance with the city's zoning regulations.
Mumbai Metropolitan Region Development Authority (MMRDA): For projects in certain regions, MMRDA’s clearance is necessary.
Environmental Clearances: If the project involves significant environmental impact, an Environmental Impact Assessment (EIA) might be required.
Fire and Safety Approvals: The redevelopment must also meet fire safety regulations and codes as per the National Building Code of India.
6. Demolition of Existing Structure
Once all permissions are secured, the existing structure is demolished. In the interim, residents are typically relocated to temporary accommodation provided by the developer, usually in nearby hotels, flats, or other rented properties. The relocation should be carefully planned to avoid inconvenience to residents. In some cases, developers may offer rent compensation to ensure the residents’ comfort.
7. Construction of the New Building
With the site cleared, the construction phase begins. During this phase, the developer builds the new residential complex, using advanced construction technologies, premium building materials, and adhering to the safety and quality standards. The new structure is typically designed with modern amenities, spacious layouts, and the latest in building technology. The construction phase can take anywhere from 1-4 years, depending on the scale of the project and its complexity.
Key elements of the construction phase include:
Excavation and foundation work.
Superstructure construction.
Installation of plumbing, electrical systems, and elevators.
Landscaping and outdoor facilities.
Compliance with fire safety, earthquake-resistant standards, and other safety regulations.
8. Post-Construction Inspections and Handover
Once the construction is complete, the developer conducts an internal inspection to ensure that everything is built according to the agreed-upon plans. This includes checking for structural integrity, plumbing, electrical systems, and other essential components. Simultaneously, external inspections are carried out by authorities to ensure compliance with building codes, safety regulations, and legal requirements.
Once the project is approved by all relevant authorities, the new apartments are handed over to the residents. Each resident receives their upgraded flat, which might include additional amenities, better design, or enhanced space compared to their original apartment.
9. Possession and Documentation
After the inspection, residents receive the official possession of their new homes. The developer will provide the residents with all the necessary documentation, including:
The title deed or ownership documents.
Occupancy certificate issued by BMC, confirming that the building is safe for habitation.
Updated property tax records.
Any other legal documents related to ownership.
10. Post-Completion Maintenance
Even after the new building is ready for occupancy, the developer’s responsibility doesn't end. The developer is typically responsible for maintaining the building for a certain period, often 1-2 years, to ensure that everything functions correctly. During this period, the developer must take care of any structural issues or defects, which is covered under a warranty period. Afterward, the residents are responsible for managing the maintenance through their housing society.
In conclusion, the ongoing redevelopment in Mumbai is reshaping the city’s skyline and providing Mumbaikars with a new lease on life. As redevelopment projects continue to progress, Mumbai is expected to evolve into a more modern, sustainable, and efficient city. By improving housing quality, infrastructure, and overall livability, redevelopment plays a critical role in the city’s growth.
As one renowned architect once said, “The future belongs to those who build it.” With each redevelopment project, Mumbai is being built for a better tomorrow.
0 notes
Text
Access Control Systems Explained: Key Components, Working, and Benefits
In an age where data, assets, and human resources must be protected more than ever, the demand for advanced access control systems is on the rise. These systems are no longer just about keeping doors locked - they have evolved into comprehensive, smart technologies that secure buildings, manage entry permissions, and provide detailed access analytics.
This blog explores what access control systems are, their key components, how they work, and the core benefits they offer to modern organizations. It also discusses how companies are moving toward next-generation cloud and mobile-enabled platforms like those offered by innovative providers such as Spintly - to enhance workplace security while maintaining convenience and scalability.

What Are Access Control Systems?
At their core, access control systems are security solutions designed to restrict or grant access to physical or digital environments based on predefined rules. These systems determine who can access a certain location, when they can access it, and under what conditions.
While traditionally associated with physical spaces like offices and server rooms, today’s systems extend their functionality to include data centers, multi-tenant properties, co-working hubs, and even cloud applications.
Key Components of Access Control Systems
To understand how access control works, it's helpful to break down the essential components that make up a typical system:
1. Access Credentials
These are the methods users employ to prove their identity. Credentials can be:
RFID cards or key fobs
PIN codes
Mobile-based access (Bluetooth or NFC)
Biometric identifiers (fingerprint, facial recognition, etc.)
Mobile and biometric credentials are increasingly popular due to their security and contactless nature.
2. Access Control Readers
These devices authenticate the credentials. Readers can range from simple RFID scanners to advanced biometric readers. In smart buildings, mobile-based readers are gaining traction due to ease of use and hygiene.
3. Access Control Panel (Controller)
This is the system’s “brain,” making decisions based on the information received from readers. The controller processes data and instructs the system whether to unlock or keep the door locked.
4. Locks and Barriers
These are the physical components (like electric locks, turnstiles, or barriers) that respond to the controller’s command.
5. Software Interface
A centralized platform where administrators define access policies, manage users, monitor entry logs, and generate reports. Modern systems offer cloud-based interfaces accessible from any location—something companies like Spintly specialize in.
How Do Access Control Systems Work?
The operation of an access control system follows a straightforward flow:
User presents credential (mobile app, card, or biometric)
Reader scans credential and sends data to the controller
Controller verifies access rights
Access is granted or denied based on the policy
System logs the attempt for auditing purposes
This entire process takes less than a second and can be configured to notify security teams, track anomalies, or even trigger other systems like CCTV or alarms.
Types of Access Control Models
Different environments require different access models. Common types include:
1. Discretionary Access Control (DAC)
The owner decides who has access to what. It's flexible but can lead to inconsistent policies.
2. Mandatory Access Control (MAC)
Permissions are strictly enforced by a central authority. Common in government and military applications.
3. Role-Based Access Control (RBAC)
Access is granted based on roles within the organization—ideal for businesses of all sizes.
4. Attribute-Based Access Control (ABAC)
Grants access based on user attributes (e.g., department, time of day, location).
Benefits of Modern Access Control Systems
1. Enhanced Security
By ensuring that only authorized individuals can enter certain areas, access control systems reduce the risk of unauthorized entry, theft, and other threats.
2. Real-Time Monitoring
Admin dashboards provide real-time logs of who accessed what and when, which can be crucial during security audits or incident investigations.
3. Reduced Administrative Burden
Systems that integrate with HRMS and directory services eliminate the need for manual provisioning and revocation of access.
4. Scalability
Whether managing one site or multiple, cloud-based access control systems allow centralized control from anywhere.
5. Visitor Management Integration
Many businesses are now combining visitor and employee access into a unified system—simplifying the onboarding of guests and contractors while maintaining high security.
6. Hygiene and Touchless Convenience
Post-pandemic, the push for touchless entry is stronger than ever. Solutions that support mobile or facial recognition credentials meet this demand effectively.
Why Cloud and Mobile Are the Future of Access Control
Legacy access control systems were often tied to on-premise servers and required significant hardware investment. Today’s smarter alternatives like Spintly’s cloud-based access control systems are revolutionizing the landscape.
These systems eliminate the need for local servers, reduce IT costs, and provide seamless updates. They are also mobile-first, allowing users to unlock doors using their smartphones a feature highly appreciated in co-working spaces, modern offices, and apartment complexes.
Some key advantages of cloud-based solutions include:
Faster setup and deployment
Automatic software updates
Remote management and troubleshooting
API integrations with third-party software like visitor management and analytics
Subscription-based pricing models for easier budgeting
Use Case: A Multi-Tenant Building with Diverse Needs
Imagine managing access for a commercial building housing multiple businesses, each with different schedules, employee roles, and visitor policies. Traditional systems would require individual control panels and physical oversight.
A cloud-based, mobile-enabled system, however, allows centralized management with customizable policies per tenant. Real-time monitoring ensures visibility across all entrances, while the system integrates smoothly with elevators, parking garages, and emergency exits.
Providers like Spintly specialize in solving such multi-layered access scenarios, delivering both flexibility and control.
Conclusion
Access control systems have grown from simple locks and keys to intelligent platforms that blend security, convenience, and efficiency. As businesses strive for digital transformation, having a secure, scalable, and user-friendly system is not just a luxury - it's a necessity.
While choosing the right system depends on your organization’s needs, those looking for future-ready solutions are increasingly moving toward cloud-based, mobile-first access control systems. Solutions from companies like Spintly are empowering organizations across industries to manage access effortlessly, gain real-time insights, and scale with confidence.
The future of workplace security isn’t just about keeping intruders out - it’s about creating seamless, intelligent, and secure environments for everyone inside.
#access control solutions#mobile access#accesscontrol#access control system#spintly#biometrics#smartacess#visitor management system#smartbuilding
0 notes
Text
Apollo TV: A Modern Alternative to Traditional Television
Apollo TV is an IPTV-based streaming service that provides access to live television channels, movies, series, and sports content. It offers a digital solution for users seeking more apollo tv control, flexibility, and variety in their viewing experience without being tied to traditional cable or satellite TV. Known for its wide content selection and user-focused features, Apollo TV has become a favored option for those looking to cut the cord and move toward online entertainment.
What Is Apollo TV?
Apollo TV is a subscription-based service that delivers television programming over the internet. Unlike conventional broadcasting methods, IPTV services like Apollo TV use high-speed connections to stream content directly to compatible devices. This allows users to watch live channels, stream movies on demand, and access international content from the comfort of their home or on the go.
The service is built around convenience and content variety. It is designed for users who want the freedom to choose what they watch and when they watch it, without the limitations of preset TV schedules.
Content and Categories
Apollo TV offers an extensive library of content across multiple genres and languages. Some of the most common categories include:
Live TV channels from the United States, United Kingdom, Canada, and other international markets
Sports networks covering both local and global events
News channels offering 24/7 coverage
Entertainment channels for series, reality shows, and talk shows
A large collection of movies, ranging from classics to the latest releases
Dedicated sections for kids’ programming, documentaries, and lifestyle content
This wide variety ensures that users of all ages and preferences can find something that suits their interests.
Features and Functionality
Apollo TV includes a number of features aimed at improving the viewing experience:
High-definition and 4K video support for superior image quality
An electronic program guide (EPG) to help users see what’s currently airing and what’s coming up next
On-demand playback for movies and series
Multi-device support for users who want to watch on more than one screen
Easy navigation with categorized menus, search functionality, and favorites lists
Compatibility with IPTV apps such as IPTV Smarters and TiviMate for broader access
The service also incorporates buffering protection and stability enhancements to reduce interruptions during streaming.
Device Compatibility
One of the strengths of Apollo TV is its ability to work across a range of devices. This includes:
Android smartphones and tablets
Android TV and smart TVs
Amazon Fire TV devices
Computers using Android emulators
iOS devices through third-party IPTV players
Streaming boxes and sticks
The ability to use the service on multiple platforms makes it easy for users to enjoy their favorite content at home or while traveling.
Subscription and Access
To use Apollo TV, users must purchase a subscription. Plans are typically offered in monthly, quarterly, and annual formats, with discounts available for longer commitments. Some packages support multiple devices, which is ideal for families or shared households.
Upon subscribing, users receive login credentials that include a username, password, and server URL. These credentials are used to access the service through the Apollo TV App or other compatible IPTV applications.
Why Choose Apollo TV?
Apollo TV stands out for its content diversity, user-friendly setup, and high-quality streaming performance. It appeals to viewers who are tired of expensive cable bills and limited programming choices. With flexible subscription options and reliable streaming, Apollo TV is positioned as a valuable choice for modern digital entertainment.
Final Thoughts
Apollo TV represents a shift in how people access and enjoy television content. By offering a broad selection of channels, on-demand media, and premium features in one platform, it delivers an efficient and customizable viewing experience. Whether you’re a sports fan, a movie lover, or just someone looking for an affordable way to stream TV, Apollo TV provides a convenient solution tailored to today’s digital lifestyle.
0 notes
Text
Defending the Digital Frontier: Key Skills Validated by a Cloud Security Certification
In 2025, the cloud isn't just a technology; it's the new digital frontier, powering everything from innovative startups in Shela, Gujarat, to the mission-critical operations of global enterprises. However, with unprecedented scalability and agility comes a unique and complex set of security challenges. Protecting these dynamic, distributed environments demands a specialized skillset – one that traditional cybersecurity alone often cannot fully address. This is why a cloud security certification has become the gold standard, not just for demonstrating knowledge, but for validating the precise cloud security skills essential for defending this crucial digital landscape.
For professionals looking to build a resilient cloud security career, understanding the core and emerging skills required is paramount. This guide will delve into the critical cloud security skills that are highly valued by employers, explain how a cloud security certification validates these competencies, and highlight why these credentials are indispensable for safeguarding data and applications in the cloud era.
Why Specialized Cloud Security Skills Are Paramount
The intricacies of cloud computing necessitate a distinct approach to security, setting it apart from traditional on-premise models. Here’s why possessing specialized cloud security skills is non-negotiable:
Shared Responsibility Model: Unlike on-premise where organizations control everything, the cloud operates on a shared responsibility model. Understanding this model and knowing whose responsibility it is to secure what (e.g., the cloud provider secures the infrastructure, the customer secures data and configurations) is foundational.
Dynamic and Ephemeral Resources: Cloud environments are highly agile. Virtual machines, containers, and serverless functions are spun up and down rapidly, often automated. Security needs to be integrated into this dynamic flow, requiring skills in automation, Infrastructure as Code (IaC) security, and continuous monitoring.
Distributed Nature: Cloud services are distributed across regions and availability zones. Securing this vast, interconnected network requires different network security paradigms compared to a centralized data center.
Cloud-Native Services and Tools: Each cloud provider (AWS, Azure, GCP) offers a unique suite of security services and tools (e.g., AWS Security Hub, Azure Sentinel, Google Security Command Center). Proficiency in these specific tools is crucial for effective cloud defense.
New Attack Vectors: Cloud environments introduce new attack surfaces, such as misconfigured S3 buckets, insecure APIs, or compromised cloud credentials. Specialized skills are needed to identify and mitigate these specific threats.
Compliance in the Cloud: Regulatory frameworks like India's DPDPA, GDPR, and HIPAA apply to cloud data. Implementing and proving compliance in a dynamic cloud environment requires specific expertise.
Core Cloud Security Skills Validated by Certifications
Leading cloud security certifications are meticulously designed to validate a comprehensive array of cloud security skills that directly address the challenges above. These include:
Identity and Access Management (IAM): This is foundational. You'll master skills in managing user identities, defining roles and permissions, implementing multi-factor authentication (MFA), and ensuring the principle of least privilege across cloud resources. This includes understanding federated identity and integrating corporate directories with cloud IAM.
Network Security in the Cloud: Key skills include designing and securing Virtual Private Clouds (VPCs) or Virtual Networks (VNets), configuring network segmentation, implementing security groups and Network Access Control Lists (NACLs), setting up cloud-native Web Application Firewalls (WAFs), and securing connectivity via VPNs or direct connect services.
Data Protection and Encryption: Validated skills involve implementing encryption for data at rest (e.g., using Key Management Services like AWS KMS, Azure Key Vault, Google Cloud KMS) and in transit (e.g., TLS for API endpoints). Understanding data classification, data loss prevention (DLP) strategies, and secure data storage practices (e.g., secure S3 buckets) is paramount.
Logging, Monitoring, and Auditing: Proficiency in configuring cloud-native logging services (e.g., AWS CloudTrail, Azure Monitor, Google Cloud Logging), integrating with Security Information and Event Management (SIEM) systems, analyzing security logs, and setting up alerts for suspicious activity. Skills in continuous monitoring and threat detection are validated here.
Compliance and Governance: Cloud security certifications validate your ability to understand and implement security controls that meet various regulatory frameworks (like India's DPDPA, ISO 27001, SOC 2). This includes establishing security policies, conducting audits, and ensuring adherence to industry best practices and cloud security posture management (CSPM).
Incident Response and Forensics in the Cloud: Skills in detecting, analyzing, containing, eradicating, and recovering from cloud-specific security incidents. This involves understanding cloud-native forensic tools and processes for investigating breaches in a distributed cloud environment.
Application Security in the Cloud: Validated skills include securing cloud-native applications, understanding API security, securing serverless functions (e.g., AWS Lambda, Azure Functions), and implementing container security (e.g., Docker, Kubernetes).
Cloud Risk Management: Identifying cloud-specific risks, conducting threat modeling exercises for cloud deployments, and implementing appropriate mitigation strategies.
Beyond the Core: Emerging Cloud Security Skills Validated
As cloud technology rapidly evolves, so do the required security skills. Leading cloud security certifications increasingly incorporate and validate expertise in these emerging areas:
DevSecOps Automation: The ability to integrate security into every phase of the software development lifecycle (SDLC) within cloud environments. This includes skills in Infrastructure as Code (IaC) security, security automation tools (e.g., Terraform, CloudFormation), and embedding security into CI/CD pipelines.
Multi-Cloud and Hybrid Cloud Security: As organizations often use more than one cloud provider or integrate cloud with on-premise infrastructure, skills in securing diverse, heterogeneous cloud environments are critical.
AI/ML in Cloud Security: Understanding how Artificial Intelligence and Machine Learning are leveraged for advanced threat detection, anomaly analysis, and automating security operations within cloud platforms.
Serverless and Container Security: Specific expertise in securing these modern, highly scalable, and often ephemeral computing paradigms, which present unique security challenges compared to traditional virtual machines.
Cloud-Native Security Services: Deep proficiency in the rapidly expanding suite of security services offered by each major cloud provider (e.g., AWS WAF, Azure Firewall, Google Cloud Armor).
How Cloud Security Certifications Validate These Skills
A reputable cloud security certification serves as a robust validation mechanism for these essential cloud security skills through:
Rigorous Exam Blueprints: Certifications base their exams on meticulously defined blueprints that directly reflect industry-demanded skills and knowledge areas.
Performance-Based Assessments: Many advanced cloud security certification exams include hands-on labs or simulations, requiring candidates to demonstrate actual proficiency in configuring, troubleshooting, or deploying security controls in a live cloud environment. This is a critical differentiator.
Comprehensive Training Paths: Certification bodies and their authorized training partners offer structured cloud security training and cloud security courses designed to impart these skills, often including extensive lab work and real-world scenarios. EC-Council, for instance, emphasizes practical learning in their programs, such as the C|CSE (Certified Cloud Security Engineer), which includes significant lab components across multiple cloud providers.
Industry Recognition: When a cloud security certification is widely recognized, it means industry experts, employers, and recruiters trust that the certified individual possesses the validated skills to perform effectively.
Choosing the Right Cloud Security Certification to Validate Your Skills
Given the array of skills required, choosing the right cloud security certification is a strategic decision that depends on your current expertise and career aspirations. Whether you're aiming for a foundational understanding or deep specialization, there's a certification designed to validate specific competencies. For a comprehensive overview of the different credentials and their skill validations, exploring the ultimate guide to the best cloud security certifications in 2025 can provide invaluable insights, helping you to align your learning path with the most sought-after skills in the industry.
The Impact of Validated Skills on Your Cloud Security Career
Possessing validated cloud security skills through a cloud security certification has a profound impact on your career:
Increased Employability: You become a highly attractive candidate for roles where cloud security expertise is a prerequisite.
Higher Earning Potential: Employers are willing to pay a premium for certified professionals who can secure their critical cloud assets.
Ability to Tackle Complex Projects: Your validated skills enable you to confidently take on challenging cloud migration, deployment, and security projects.
Contribution to Organizational Resilience: You become a key player in defending your organization against sophisticated cloud-native threats, directly contributing to its business continuity and reputation.
Clear Career Trajectory: Certified skills provide a strong foundation for continuous learning and progression into more advanced and specialized roles within the cloud security career path.
Conclusion
In 2025, defending the digital frontier requires a specialized arsenal of cloud security skills. From mastering Identity and Access Management and network security in the cloud to understanding compliance and automating security controls, these competencies are vital for safeguarding modern digital infrastructure. A cloud security certification serves as the definitive validator of these crucial skills, proving to employers that you possess the practical abilities needed to excel. By strategically acquiring and validating these key cloud security skills, you position yourself at the forefront of a high-demand industry, ready to protect the most valuable assets in the digital age.
0 notes
Text
Cloud Security Market Emerging Trends Driving Next-Gen Protection Models
The cloud security market is undergoing rapid transformation as organizations increasingly migrate their workloads to cloud environments. With the rise of hybrid and multi-cloud deployments, the demand for robust and scalable cloud security solutions is growing. Emerging trends in cloud security reflect both technological evolution and the increasing sophistication of cyber threats. These trends are reshaping how enterprises secure data, manage compliance, and maintain trust in cloud-based systems.

Zero Trust Architecture Becoming a Core Principle
One of the most significant shifts in cloud security is the adoption of Zero Trust Architecture (ZTA). Zero Trust eliminates the traditional notion of a trusted internal network and instead requires continuous verification of user identities and devices, regardless of their location. With cloud environments inherently distributed, ZTA is becoming essential. Enterprises are integrating identity and access management (IAM), multi-factor authentication (MFA), and micro-segmentation to strengthen their security postures.
AI and ML Enhancing Threat Detection and Response
The integration of artificial intelligence (AI) and machine learning (ML) in cloud security tools is accelerating. These technologies are being used to detect anomalies, automate threat responses, and provide real-time risk analysis. AI-driven security platforms can process massive volumes of data from cloud logs and network activities, enabling early detection of sophisticated attacks like insider threats, ransomware, or credential stuffing. Predictive analytics is also helping security teams to anticipate potential vulnerabilities and reinforce defenses proactively.
SASE and SSE Frameworks Gaining Ground
The Secure Access Service Edge (SASE) and Security Service Edge (SSE) frameworks are rapidly gaining traction. SASE combines network security functions such as secure web gateways (SWG), cloud access security brokers (CASB), and firewall-as-a-service (FWaaS) with wide-area networking (WAN) capabilities. SSE, a component of SASE, focuses on delivering security services through the cloud. These models offer centralized policy enforcement and visibility, crucial for organizations supporting remote and hybrid workforces.
Cloud-Native Security Tools on the Rise
As organizations build and deploy applications directly in the cloud, the need for cloud-native security is growing. These tools are designed to work seamlessly with cloud platforms like AWS, Azure, and Google Cloud. Examples include cloud workload protection platforms (CWPPs), cloud security posture management (CSPM), and container security solutions. They allow for automated scanning, misconfiguration detection, and policy management in dynamic environments such as containers, microservices, and Kubernetes.
Shift-Left Security Practices Becoming Standard
In response to increasing DevOps adoption, Shift-Left security is emerging as a best practice. This trend involves integrating security earlier in the software development lifecycle (SDLC), ensuring that vulnerabilities are addressed during code development rather than post-deployment. Tools like automated code scanning, infrastructure as code (IaC) analysis, and security-focused CI/CD pipelines are empowering developers to embed security into their workflows without slowing innovation.
Increased Emphasis on Regulatory Compliance and Data Sovereignty
Regulatory requirements are evolving globally, and organizations must ensure compliance with data privacy laws such as GDPR, CCPA, and upcoming regional cloud regulations. There is a growing trend toward data sovereignty, where governments require that data be stored and processed within specific geographic boundaries. This is pushing cloud providers to localize data centers and offer compliance-friendly security configurations tailored to regional laws.
Serverless and Edge Computing Security Gaining Focus
The expansion of serverless architectures and edge computing introduces new security challenges. These technologies reduce infrastructure management but also create ephemeral and distributed attack surfaces. Security solutions are evolving to monitor and protect functions triggered by events in real-time. Serverless security tools focus on identity-based access, runtime protection, and least privilege policies, while edge security emphasizes endpoint hardening, network segmentation, and data encryption at rest and in motion.
Third-Party and Supply Chain Risk Management
Cloud environments often rely on a vast ecosystem of third-party tools and APIs, which can introduce vulnerabilities. There is a growing focus on supply chain security, ensuring that software components and service providers adhere to strong security practices. Enterprises are increasingly conducting security assessments, continuous monitoring, and third-party audits to manage these risks effectively.
Conclusion
The cloud security market is evolving rapidly to keep pace with the complexity and scale of modern cloud infrastructure. Emerging trends such as Zero Trust, AI-driven security, SASE/SSE frameworks, and Shift-Left development practices reflect a broader movement toward adaptive, intelligent, and integrated security models. As cloud adoption accelerates, businesses must stay ahead by embracing these innovations and investing in comprehensive, forward-looking security strategies. The future of cloud security lies in being proactive, predictive, and resilient—ensuring trust, agility, and compliance in an increasingly digital world.
0 notes